POC Security System High security system combining PIN-on-Card, information security, physical access, control and alarm – all in one system. - ppt video online download

Riassunto: Guardforce Security adotta la soluzione Push-to-Talk di Hytera per migliorare l'efficienza operativa | Business Wire
GitHub - UT-Security/cve-2023-5217-poc: A PoC to trigger CVE-2023-5217 from the Browser WebCodecs or MediaRecorder interface.
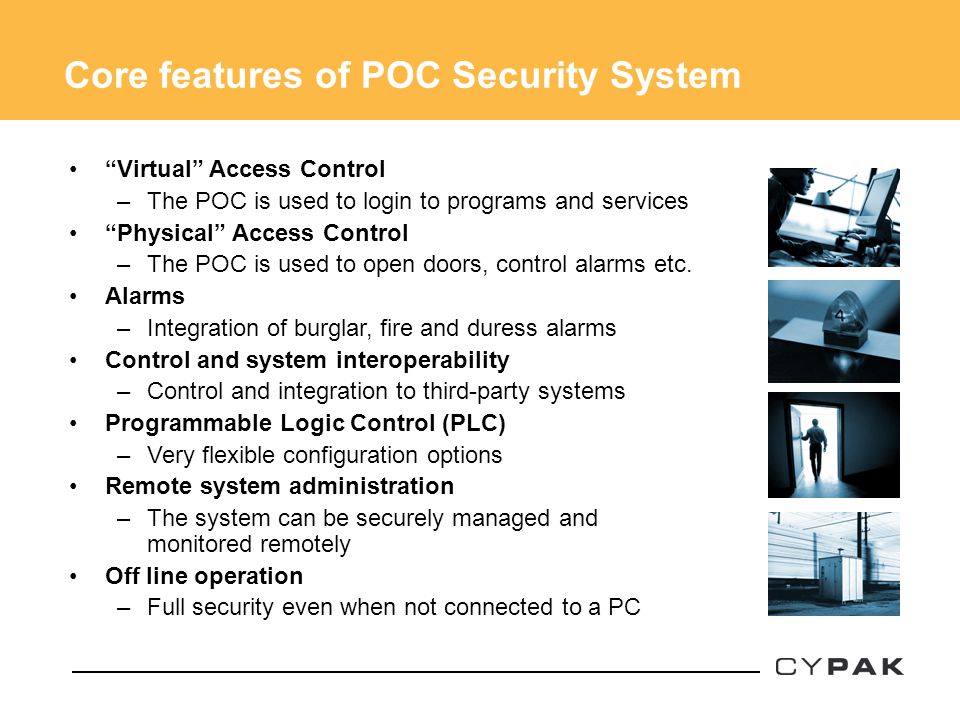
POC Security System High security system combining PIN-on-Card, information security, physical access, control and alarm – all in one system. - ppt video online download

POC Axion Spin, Casco da Bici, XS-S (51-54 cm), Rosa (Actinium Pink Matt) : Amazon.it: Sport e tempo libero

POC Axion, Casco da Bicicletta Unisex Adulto, Uranium Black Matt, L (59-62cm) : Amazon.it: Sport e tempo libero

POC Axion Spin, Casco da Bici, XS-S (51-54 cm), Bianco (Matt White) : Amazon.it: Sport e tempo libero